Actions
NAC-ABE Design » History » Revision 2
« Previous |
Revision 2/13
(diff)
| Next »
Suravi Regmi, 11/21/2025 08:29 PM
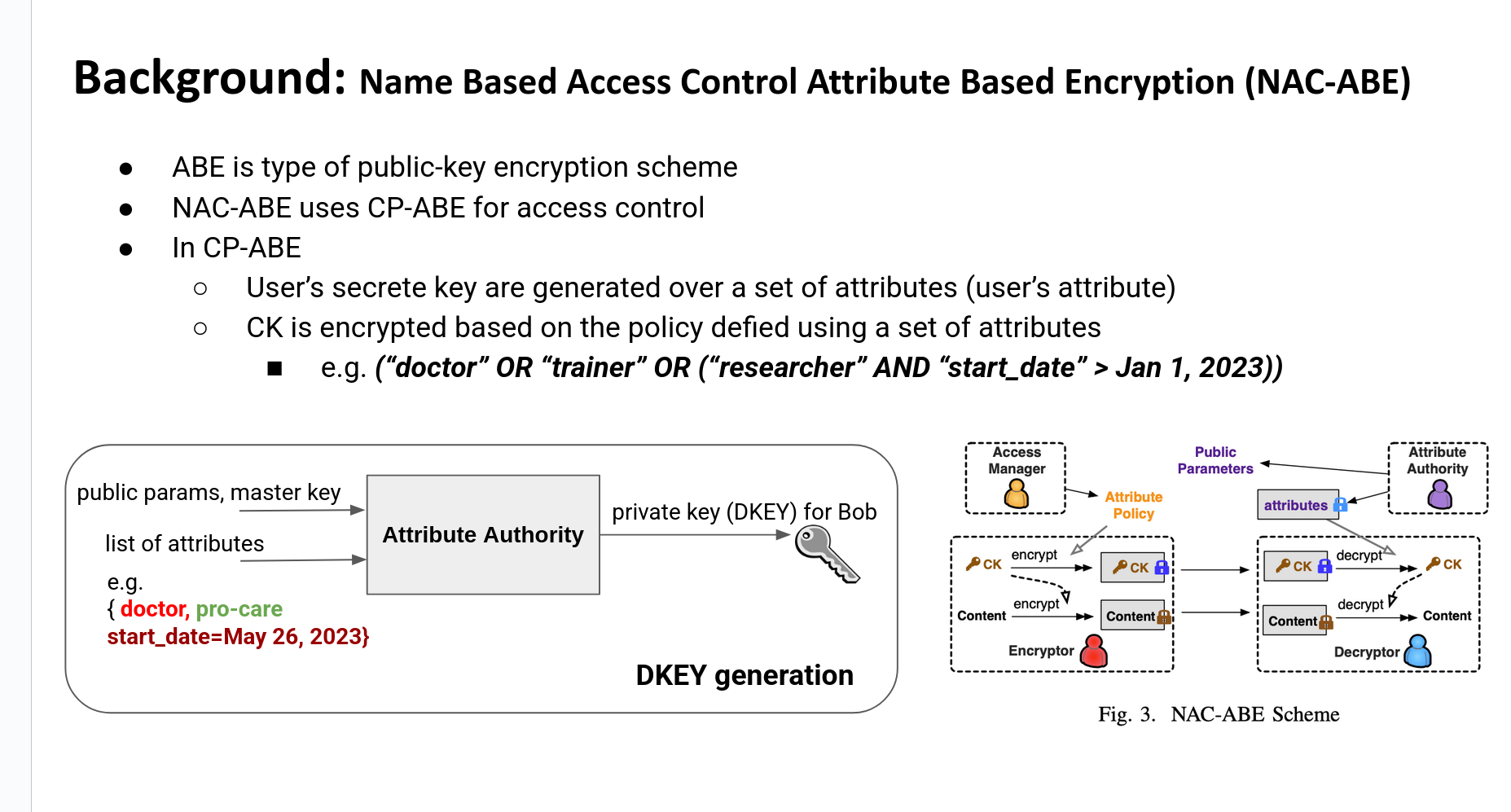
NAC-ABE Design¶
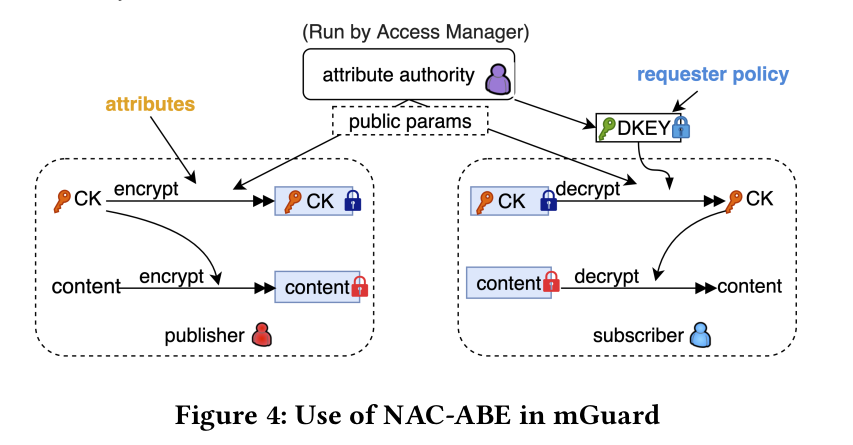
Why KP-ABE
Data encryption → CK encryption → CK decryption
ABE encryption of CK (black box)
ABE key issuance (DKEY)
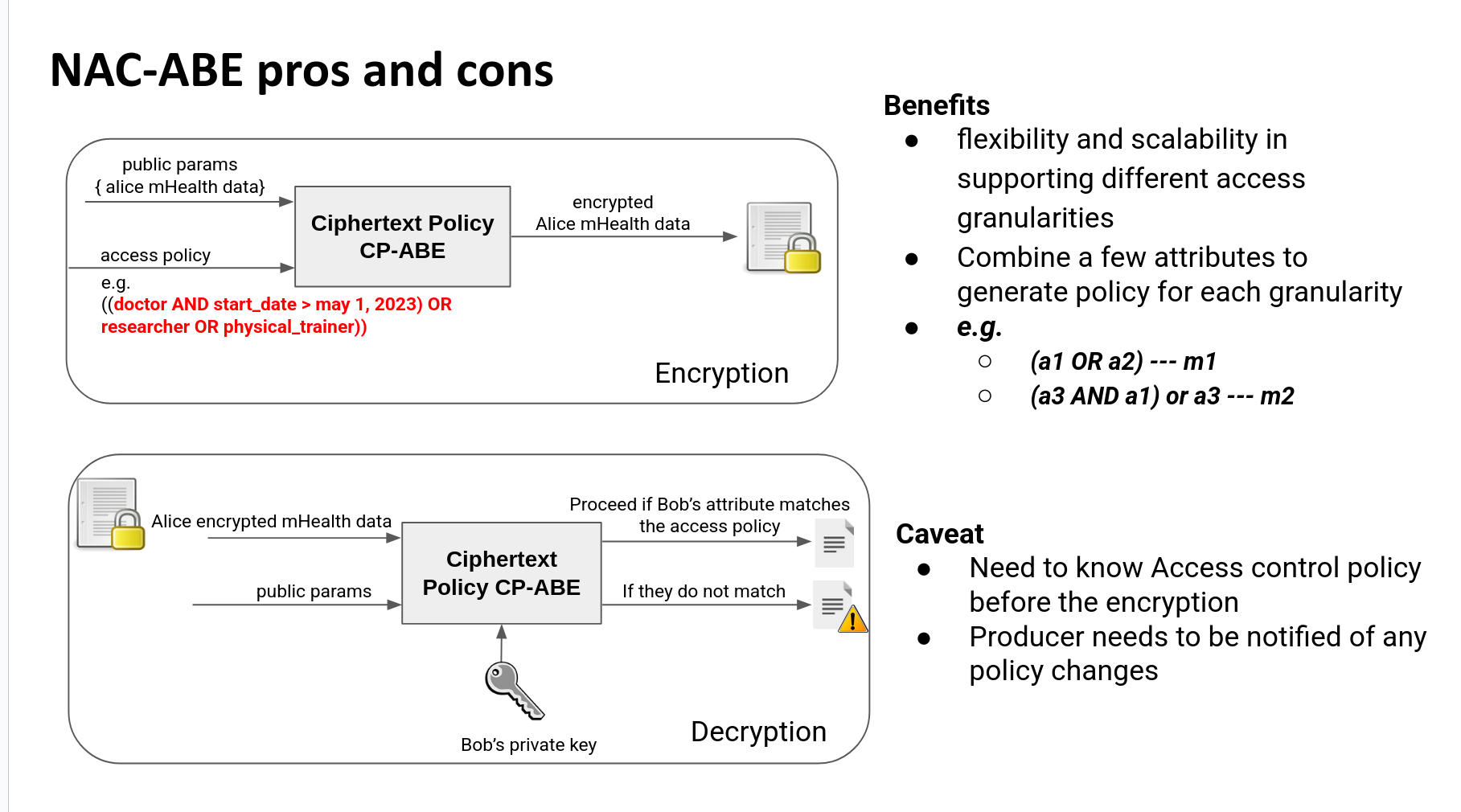
CK granularity (second/minute/hour)
Tradeoffs of CK reuse level
Updated by Suravi Regmi 3 months ago · 13 revisions